How are environmental characteristics accounted for when analysing vulnerabilities?
In the previous blog, we looked at the simple steps to enable Application security in Dynatrace. In this article, we will look at how the AI accounts for the environmental characteristics for given vulnerabilities to accurately rate the risk level.
Analysing Vulnerabilities:
With Application Security enabled and configured, Dynatrace will report vulnerabilities analysing additional contextual information like exposure to the internet, access to sensitive data(DB) etc.
Needless to say, this is in addition to Infrastructure, Application, Real User Monitoring that Dynatrace already provides.
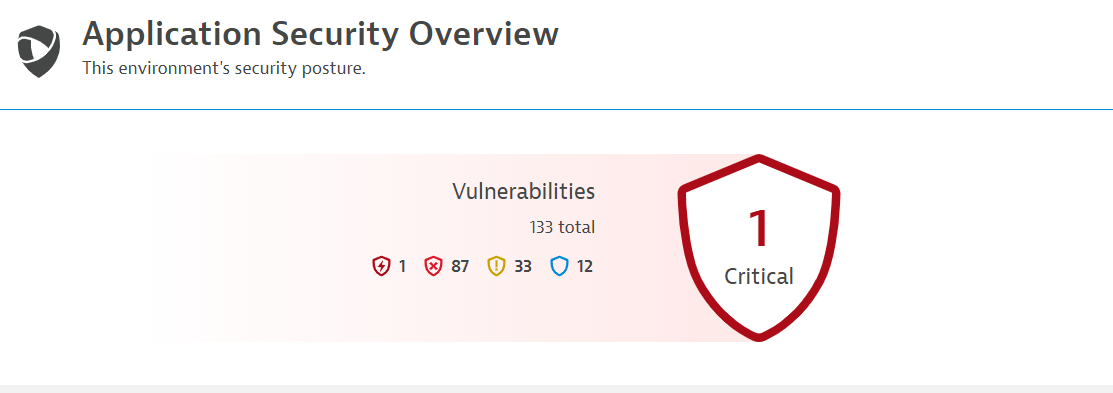
Below is a screenshot of the Application Security Overview page:
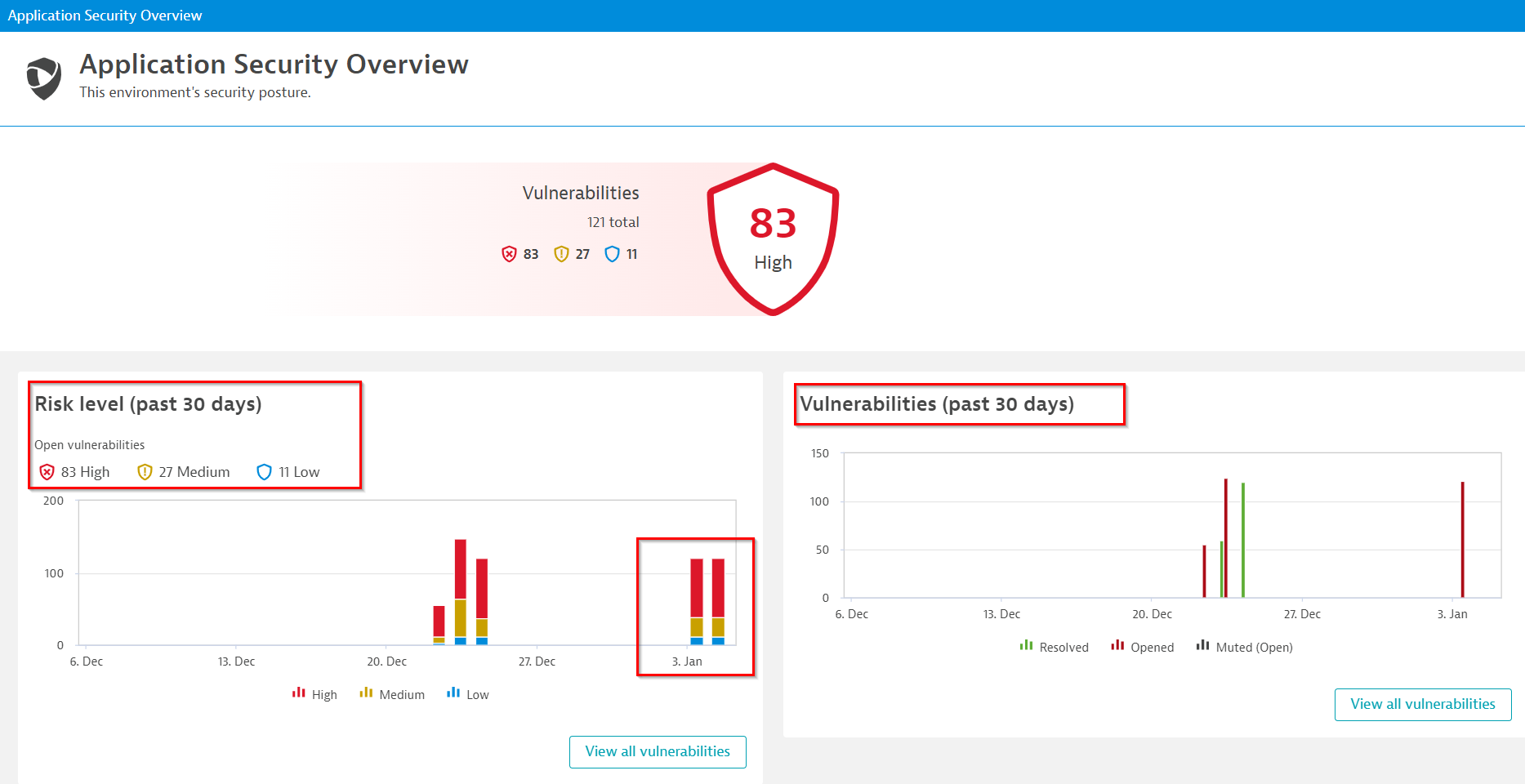
By clicking on View all vulnerabilities button, you would see all the vulnerabilities. You can even filter the vulnerabilities seen on a specific host. In the below example, I have looked up vulnerabilities in the specific host based on the hostname:
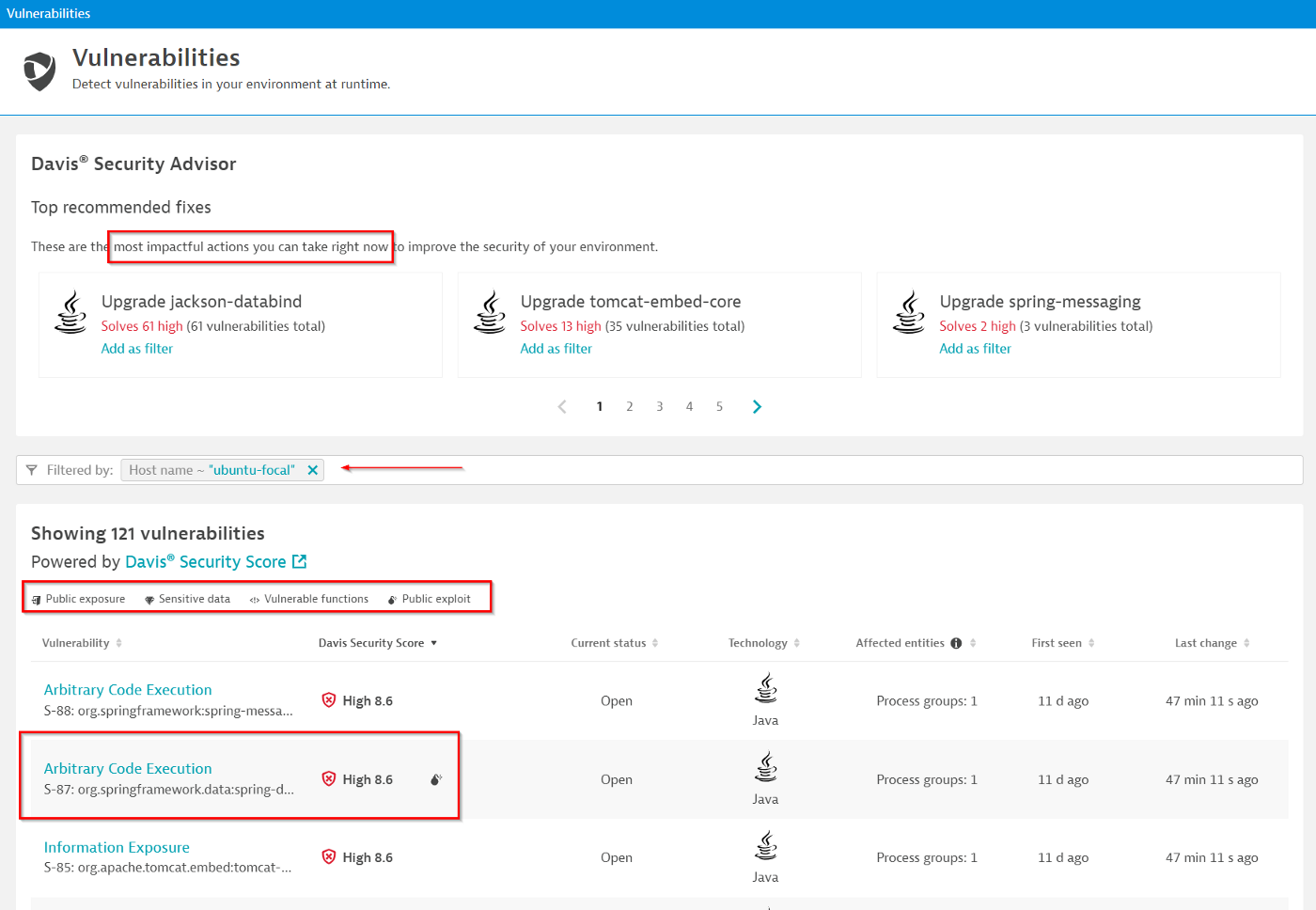
Let’s take a look into the vulnerability. You may want to open the image in a new tab to see it on full screen.
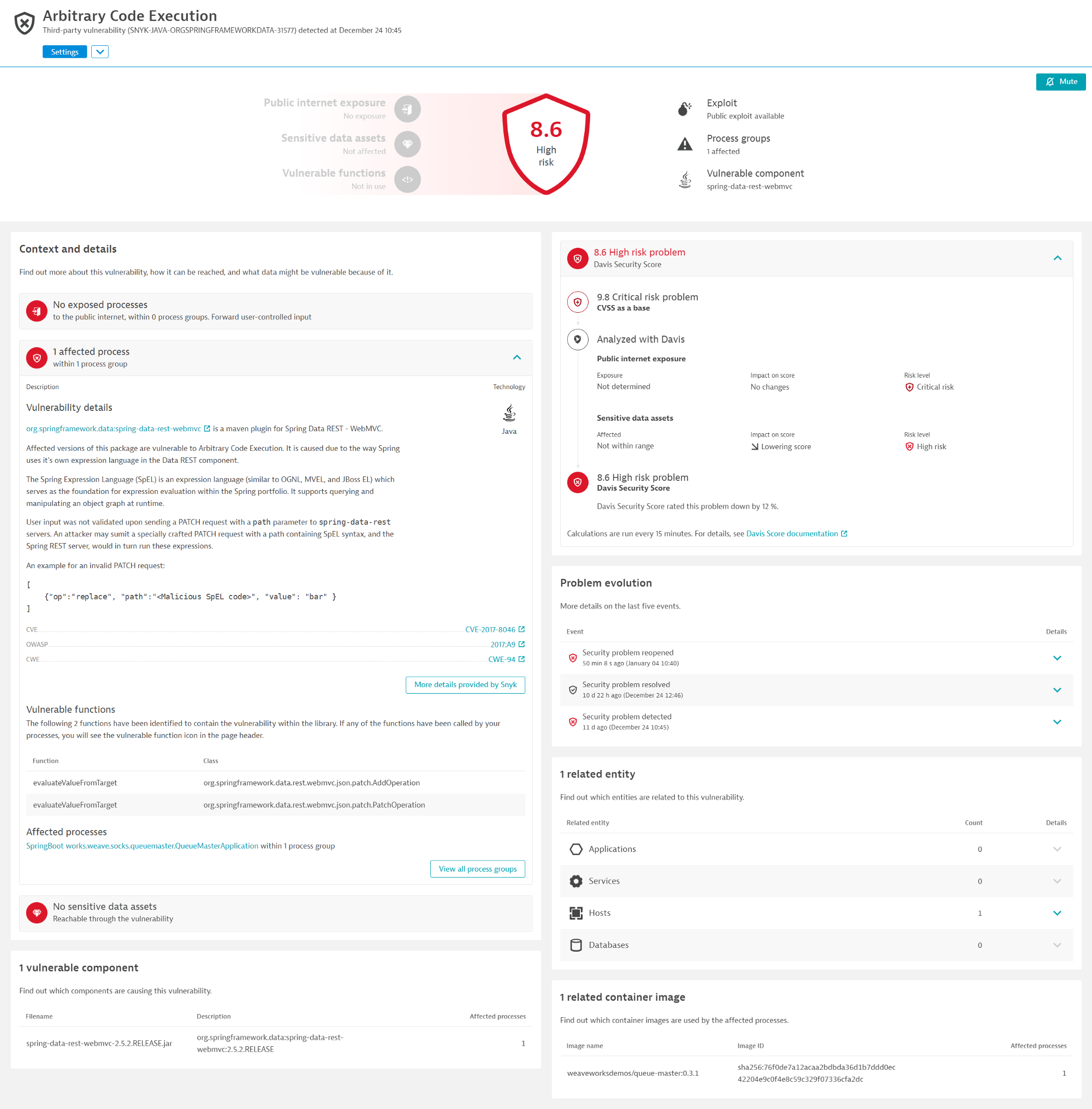
The above screenshot shows information not just about the vulnerability but most importantly it tells me that:
- there may or may not be public exposure(more accurately in the next sections),
- the vulnerability is not affecting any sensitive data and
- the vulnerable functions are not in use.
Davis Security score(DSS):
Dynatrace has calculated a Davis Security score for this vulnerability which is an enhanced risk-calculation score based on the industry-standard Common Vulnerability Scoring System. Because Davis AI also considers parameters like public internet exposure and checks to see if and where sensitive data is affected, DSS is the most precise risk-assessment score available.
DSS is more accurate: Davis doesn’t assume the worst-case scenario. Instead, Davis adapts the characteristics of the vulnerability to your particular environment, taking into consideration its structure and topology, and advises you as to which elements are prone to errors and how to handle security issues. With Davis AI, you can find out if the affected entity is reachable from the Internet and if there is any data stored in reach of an affected entity.
DSS makes you more efficient: By including additional parameters in its analysis, Davis can more precisely calculate the security score and predict the potential risk of a vulnerability to your environment. By reducing the score of vulnerabilities that are, in fact, not critical for your environment, you gain time to focus on the real issues and fix them faster.
Why does the same vulnerability have different DSS scores?
The table below shows how DSS provides an accurate assessment of the Log4j vulnerability based on the environment of the affected system. Although the CVSS score for the vulnerability is 9.8, DSS doesn’t assume the worst-case scenario and does a true assessment.
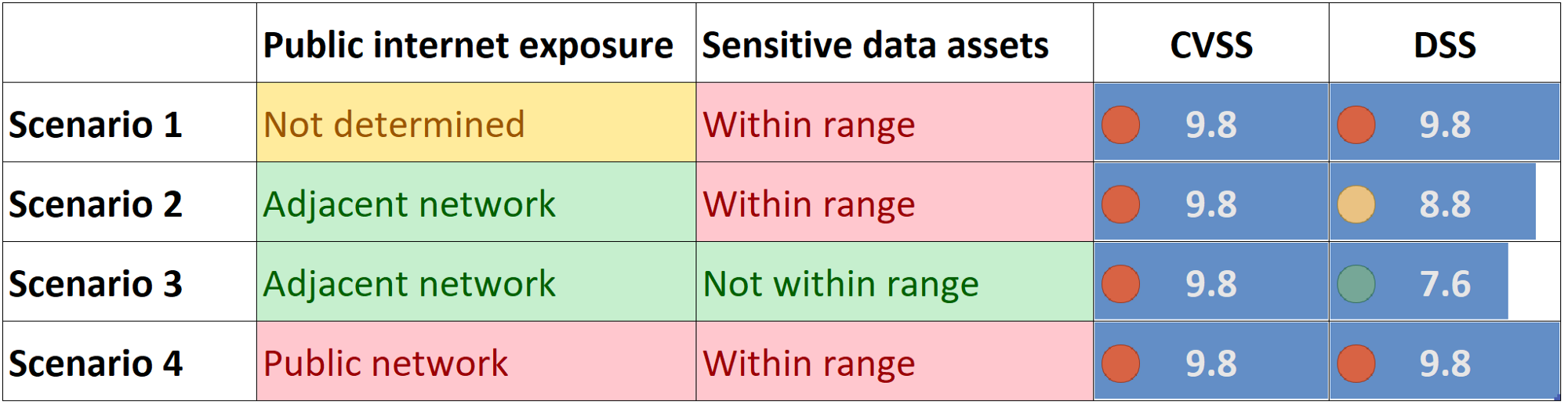
In the next section, I will show you how each of the scenarios looks like and how you could use DSS for precise risk assessment.
Log4j
In the same Linux machine, I installed a Java Application that used the infamous Log4j library for logging. Within no time, I see Dynatrace detected and rated the vulnerability as critical:
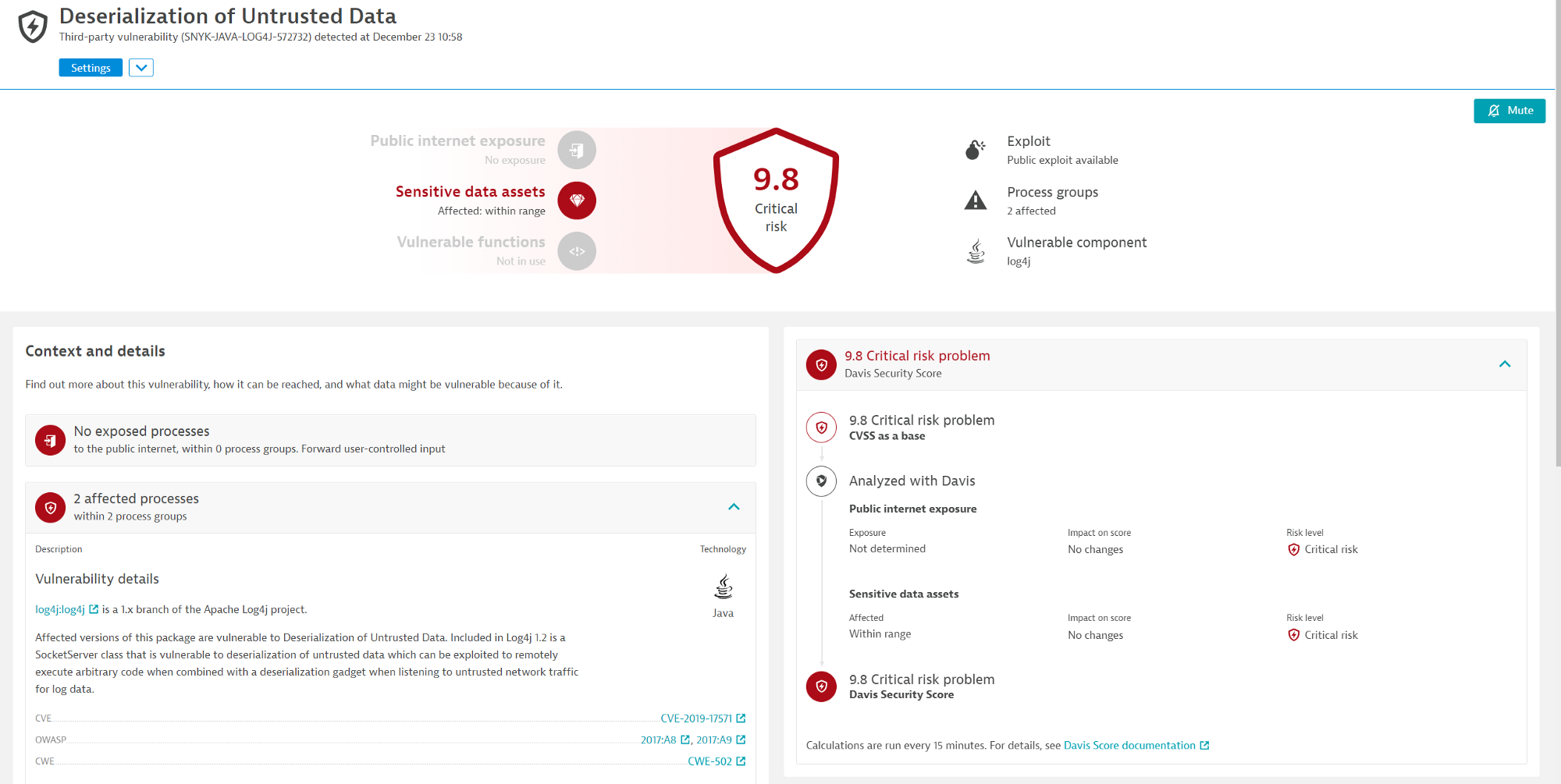
Note in the below screenshot, Davis has marked that the vulnerability with symbols to indicate that it has access to sensitive data and there is a known malicious code that exploits this vulnerability.
![]()
Note that this time, we see that this vulnerability has the sensitive data assets symbol enabled and it has a critical DSS score.
Same Vulnerability but varying DSS depending on exposure and sensitivity
In the below example we see a score of 9.8 which matches the CVSS base score but you could see that the exposure to other internet was not determined but sensitive data was within range
Scenario 1
Log4j Vulnerability with sensitive data assets and undetermined public exposure: Critical risk(score 9.8)
- Public internet exposure: Not determined
- Sensitive data assets: Within range
- CVSS Score: 9.8
- DSS Score: 9.8 (critical risk) DSS is unchanged because of undetermined public internet exposure
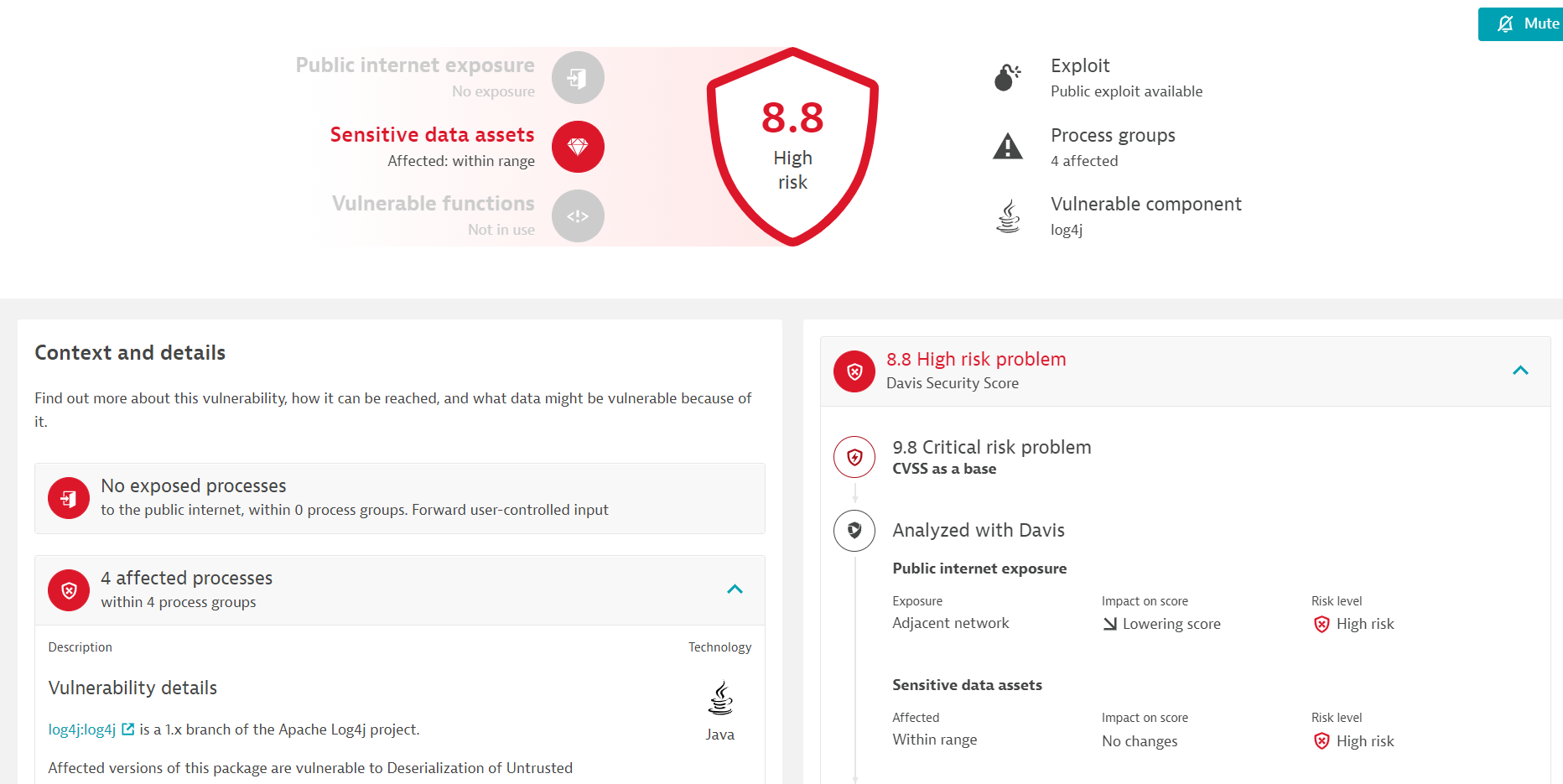
Scenario 2
Log4j Vulnerability with sensitive data assets and exposure to Adjacent network: High risk(score 8.8)
- Public internet exposure: Adjacent network
- Sensitive data assets: Within range
- CVSS Score: 9.8 (no change)
- DSS Score: 8.8 (critical risk) score less than CVSS
In the below example for the same vulnerability, Davis has lowered the score because the attack vector(exposure) is an Adjacent network. An adjacent network means the attacker must be on the same network. The sensitive data assets are within range and it is still a high risk.
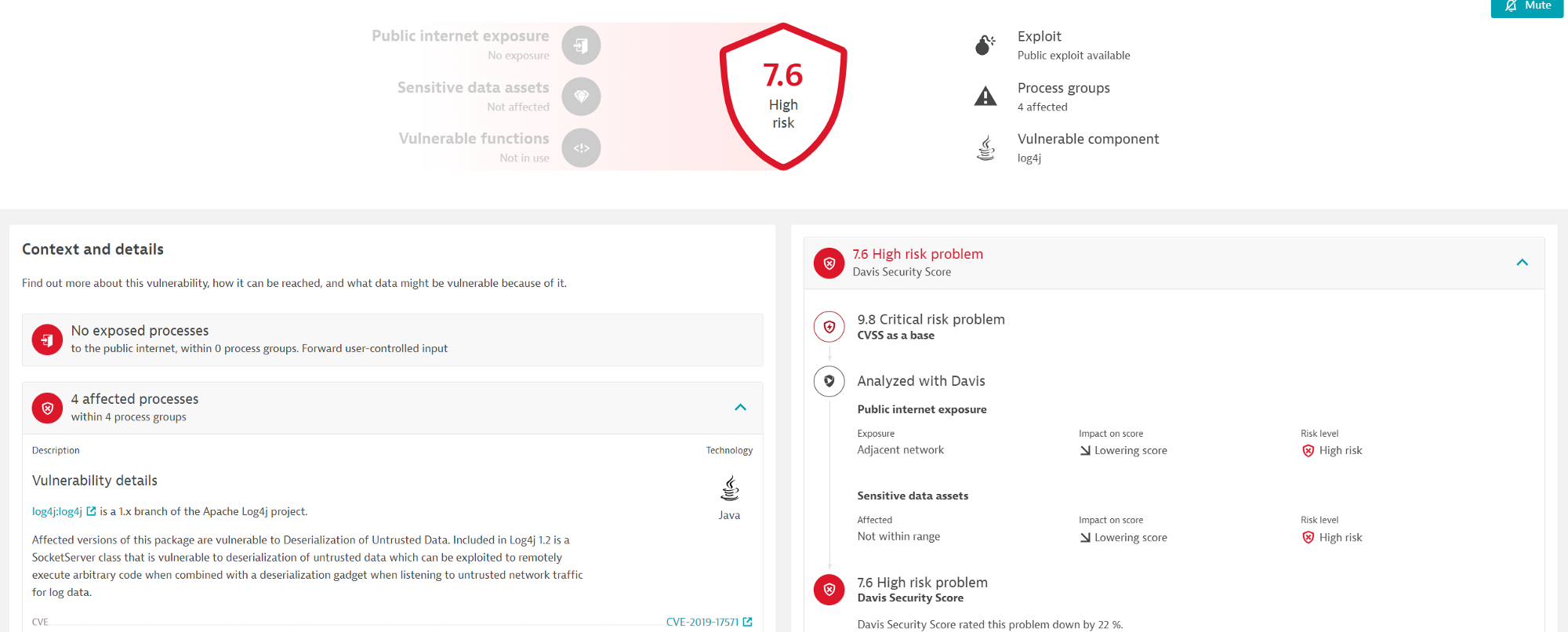
Scenario 3
Log4j Vulnerability with sensitive data assets not in range and exposure to Adjacent network: High risk(score 7.6)
- Public internet exposure: adjacent network
- Sensitive data assets: Not within range
- CVSS Score: 9.8 (no change)
- DSS Score: 7.6 (high risk) score less than CVSS
In the next sample scenario, we see that the exposure is to an adjacent network and sensitive data is not within range further lowering the DSS
Scenario 4
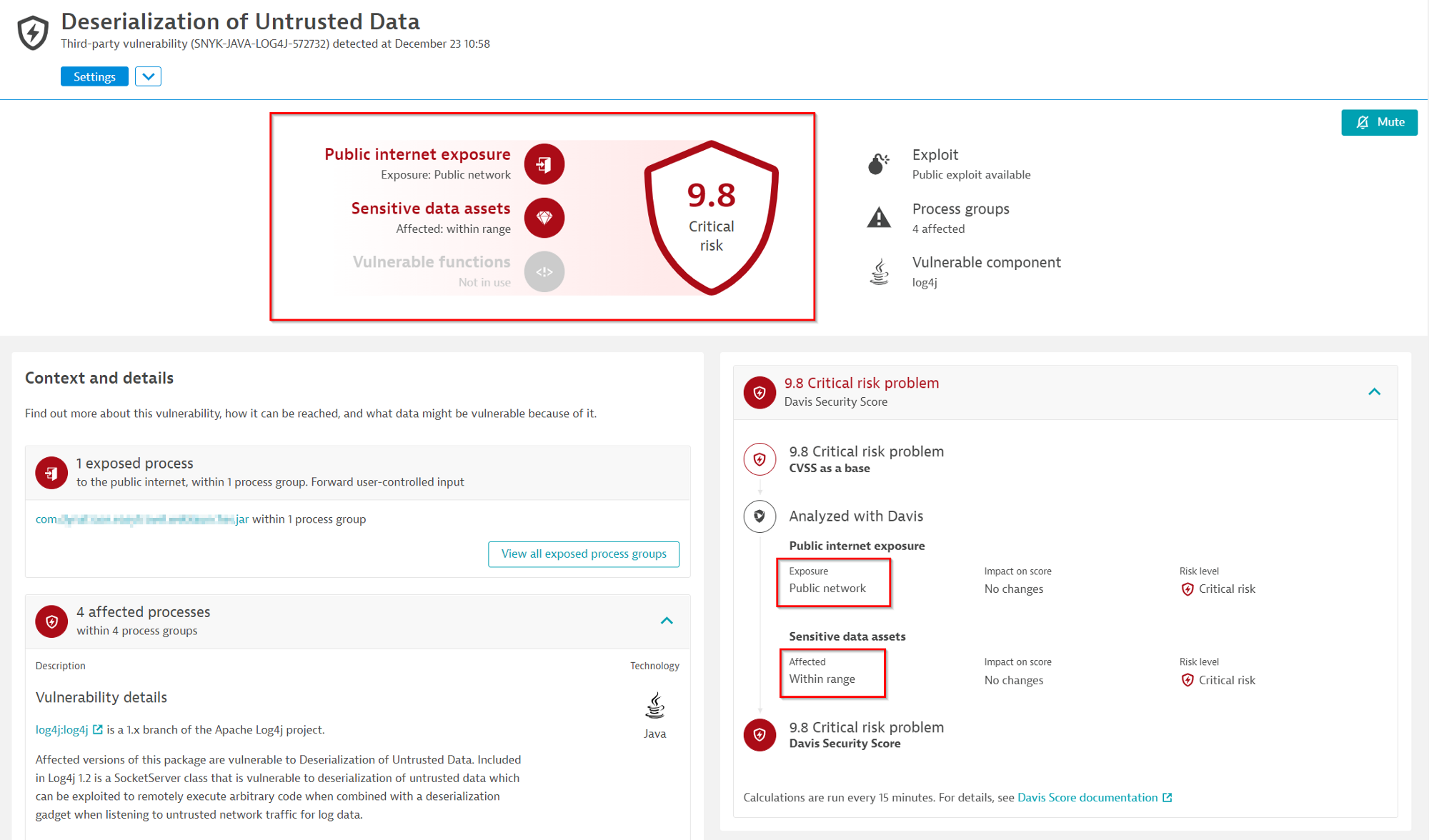
Log4j Vulnerability with sensitive data assets within range and exposure to Adjacent network: Critical risk(9.8)
- Public internet exposure: Public network
- Sensitive data assets: Within range
- CVSS Score: 9.8
- DSS Score: 9.8 (critical risk) score equals CVSS because of Public exposure
In the below example, the vulnerability is exposed to Public network and has sensitive data within range. Because of this, the DSS score is 9.8 and is categorised as Critical risk.
Why is DSS important?
In the above example, we looked at the same log4j vulnerability which has a CVSS score of 9.8, but because Davis AI considers environmental characteristics like public internet exposure and checks to see if and where sensitive data is affected, DSS is the most precise risk-assessment score available.
With a lowering score(scenarios 2 and 3) and an explanation that the attacker needs to be on the same network, you can focus on securing the network layer quickly while you work out a rollout of the patch to fix the vulnerability.
With a high score(scenario 4) and an explanation that the attacker can be on any public network, you would have to prioritise restricting the network access, securing the data and applying a patch.
Does the AI have enough data to calculate this accurately?
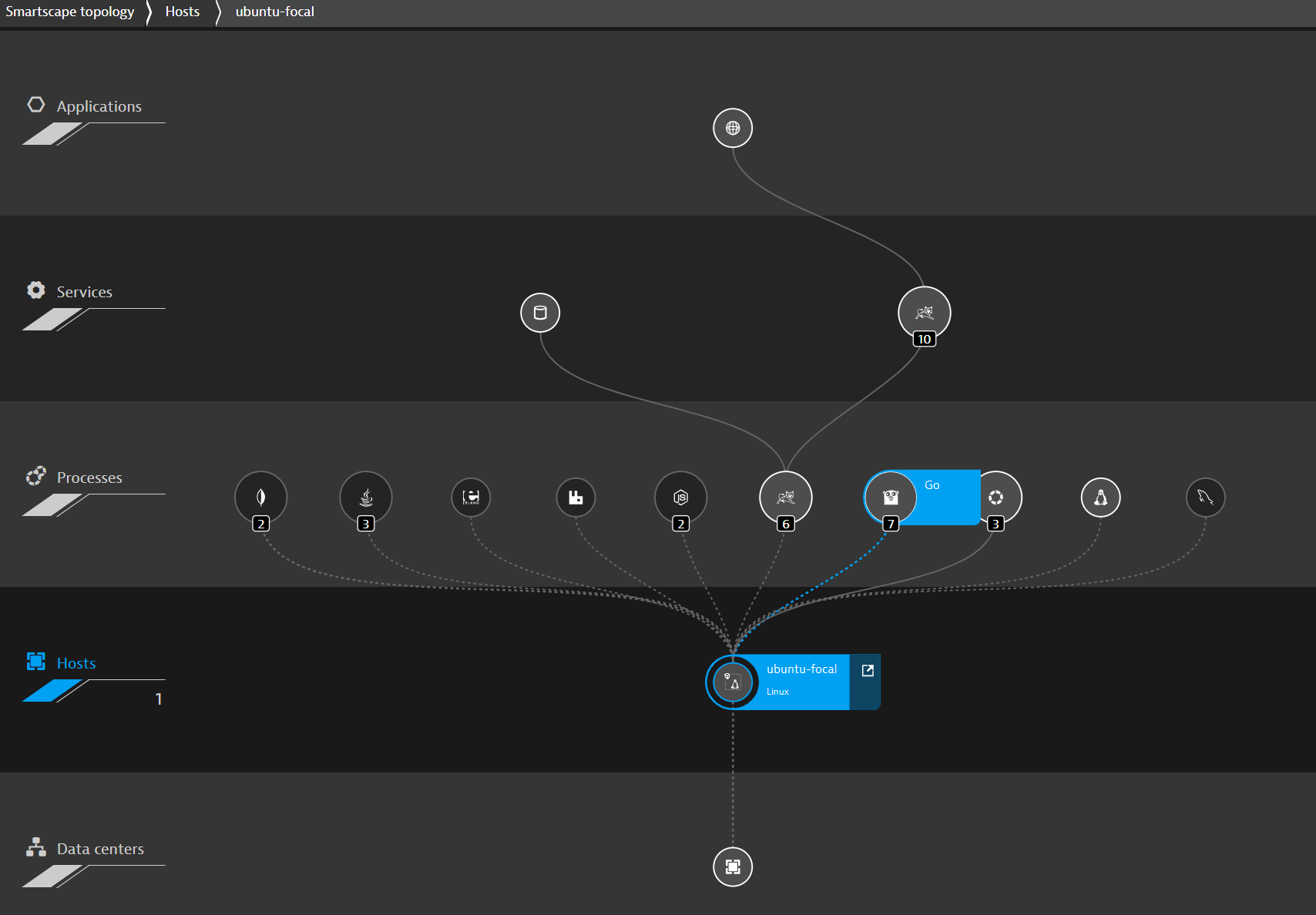
Dynatrace already has the full topology information of the application and you can verify this in the Smartscape topology. In addition, all the individual distributed transaction tracing (PurePath) looks for everything in the request from the network to code-level to calculate DSS.
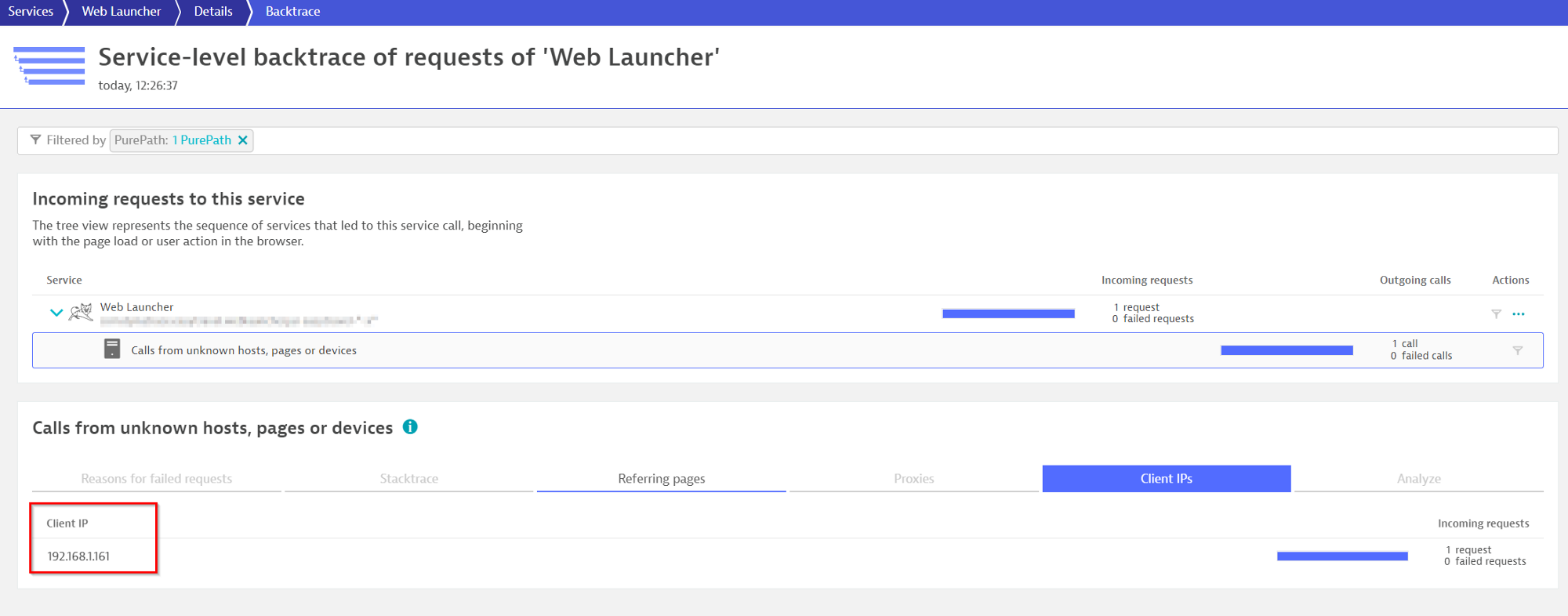
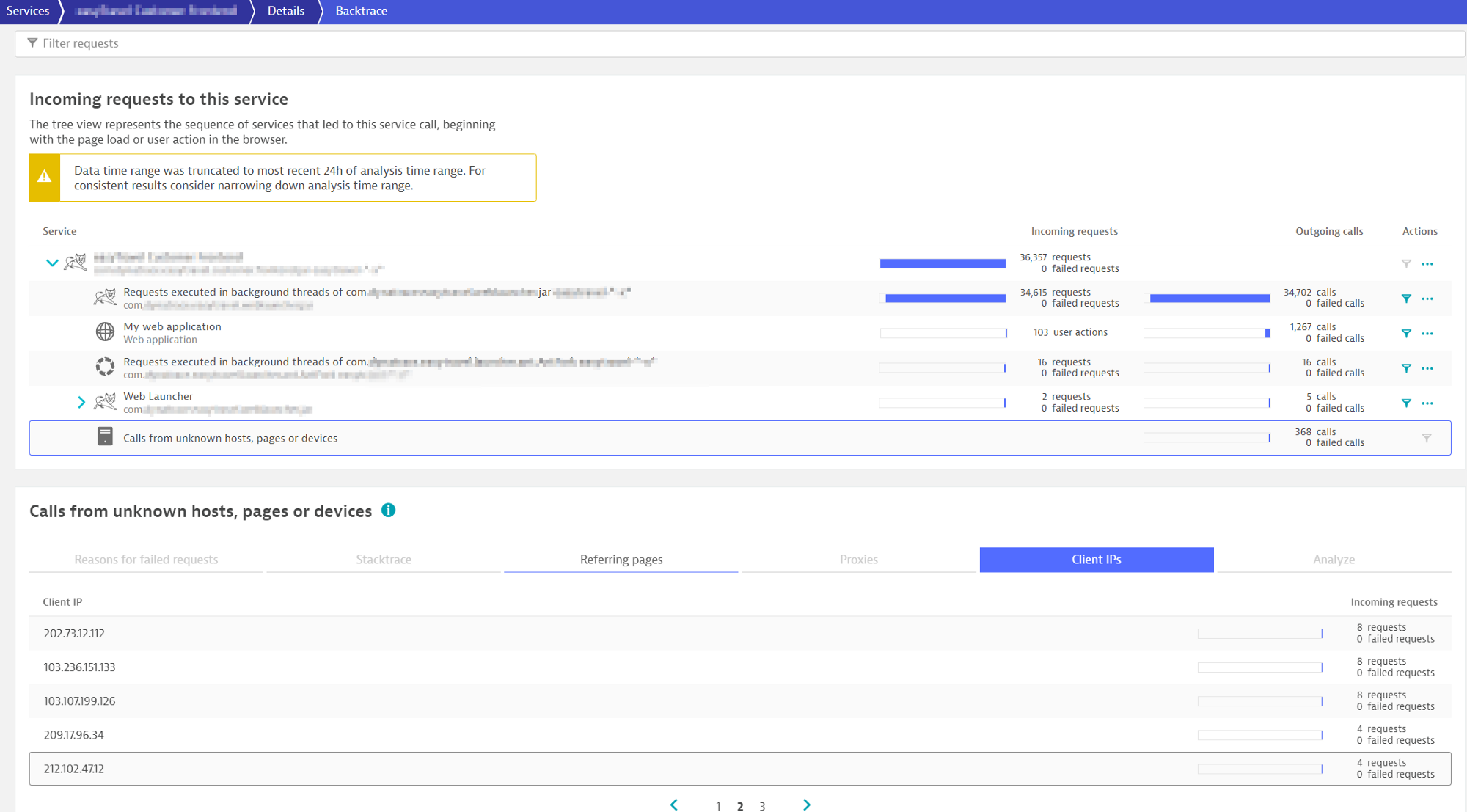
Below screenshots show the Backtrace of a request where you can identify the source IPs of the client connecting. In the first screenshot, you see a private IP while in the second you see the Public IPs.
Clients connected from Private IPs
Clients connected from Public IPs
Conclusion
It took very few clicks to enable run-time vulnerability detection and Dynatrace was able to automatically detect, categorise, calculate DSS(Davis Security Score) and provide impact for the vulnerability.
We were also able to see how the data that DSS uses is always in context and why DSS is more reliable and useful in the real world than just CVSS. Just because you have vulnerable software doesn’t mean you need to patch all of them together. Using DSS, you can now make an accurate risk assessment of your entire environment and work out a workable mitigation plan.
Further reading
Previous Blog: How to detect Vulnerabilities in Application using Dynatrace: URL
Davis Security Score calculations: URL
Adjacent Network and CVSS Scoring: URL
CVSS Scoring: URL
SmartScape Topology: URL
PurePath: URL
Davis AI: URL
Note: This article was first published on Medium by the same author